
Optimizing Radio Frequency Fingerprinting for Device Classification: A Study Towards Lightweight DL Models
https://10.1109/ICCSPA61559.2024.10794386
As the Internet of Things (IoT) permeates diverse application domains, ensuring the security of wireless networks has become increasingly critical. However, the constraints of resource-limited IoT devices render complex encryption impractical. Consequently, Radio Frequency Fingerprinting (RFF) has emerged as a promising avenue, leveraging unique device characteristics resulting from manufacturing nonlinearities. RFF enhances physical layer security by enabling device classification and authentication at IoT gateways. While deep learning (DL) aided RFF systems offer exceptional classification accuracy, their deployment on edge devices remains challenging to this end. Accordingly, there is a gap in the literature for efficient model exploration and implementation. This study proposes a lightweight Convolutional Neural Network (CNN) model using 1D convolutional filters to reduce inference latency. The model was applied to an open-source dataset comprising 30 LoRa devices. An evaluation was conducted to compare classification accuracy and inference latency using Short Time Fourier Transform (STFT) and Fast Fourier Transform (FFT) for preprocessing. Additionally, the performance of the proposed model was compared against a CNN model utilizing 2D convolutional filters. The model exhibited a significant reduction in inference latency with miniscule degradation in classification accuracy, addressing the identified gap, and propelling the academic discourse towards RFF for edge devices.

5G Beyond for Healthcare: Leveraging AI/ML and Diverse Datasets for Cybersecurity
doi.org/10.1007/978-3-031-85558-0_3
The rapid adoption of 5G networks, space networks, and Internet of Things (IoT) technologies in healthcare has significantly expanded the attack surface for cybersecurity threats. This evolving landscape demands robust defense mechanisms that can anticipate and neutralize sophisticated cyber-attacks. Artificial Intelligence (AI), Machine Learning (ML), and Deep Learning (DL) technologies are pivotal in developing such advanced cybersecurity solutions. A critical factor influencing the effectiveness of these AI/ML models is the quality and diversity of the datasets used in their training. This paper presents a systematic review of various datasets used for AI/ML-based cybersecurity model training across multiple domains, with a focus on 5G networks, IoT healthcare, and space networks. By employing a structured Goal-Question-Metric (GQM) methodology and Quasi-Gold Standard (QGS) validation, we assessed the characteristics, applications, and limitations of real, synthetic, and hybrid datasets in enhancing cybersecurity measures. The review identifies key trends, gaps, and future research directions, highlighting the need for more diverse datasets, standardized benchmarks, and privacy-preserving techniques. Our findings offer insights into improving the resilience of AI/ML models for cybersecurity, guiding the development of more effective and adaptable defense strategies across emerging network technologies.

Reducing Defense Vulnerabilities in Federated Learning: A Neuron-Centric Approach
doi.org/10.3390/app15116007
Internet of Things (IoT) devices are becoming more and more common in homes, making the security and privacy of these increasingly important. To investigate how the users’ security and privacy practices can be improved, it is necessary to understand the current everyday practices and what impacts these. In an interview study, this paper reveals that users’ practices are primarily influenced by the convenience offered by the IoT device, and the motivation and the effort required from the user to make themselves aware of the security requirements and enact change within their IoT ecosystem.
Understanding Security and Privacy Practices Around Internet of Things Devices
Internet of Things (IoT) devices are becoming more and more common in homes, making the security and privacy of these increasingly important. To investigate how the users’ security and privacy practices can be improved, it is necessary to understand the current everyday practices and what impacts these. In an interview study, this paper reveals that users’ practices are primarily influenced by the convenience offered by the IoT device, and the motivation and the effort required from the user to make themselves aware of the security requirements and enact change within their IoT ecosystem.
Integrating Cybersecurity in STEM Education: Hands-On Learning for the 5G/6G Era
This paper explores the enhancement of Science, Technology, Engineering, and Mathematics (STEM) education through the integration of network and systems security topics, and specifically hands-on, experimental learning activities. With the inclusion of real-world use cases of cybersecurity and trust topics into curricula, educators can adequately prepare their students for an era of a fully interconnected world. Strategies for curriculum design that can foster a diverse, competent workforce are discussed.

Unnamed. The phenomenon of Migrant Disaster Victim Identification in Europe.
Among the various existing case scenarios within the contexts of DVI, there is also what has recently begun to be called MDVI (Migrant Disaster Victim Identification). This terminology groups together those scenarios characterised by the mass death of migrants during the migration process, including deaths caused by shipwrecks or drowning, violence, exposure to extreme environmental conditions, lack of health care and any other aetiology as long as they occur in transit or on the migratory route. In the last 10 years alone, more than 30,000 migrants have died trying to reach Europe (mostly in shipwrecks in the Mediterranean), of which more than 23,000 have not been identified.
More Info: https://migrant-dvi.eu/

COST ASSOCIATION CUSTOMER SATISFACTION SURVEY 2025
This report presents the findings of the fifth wave of the COST Association Customer Satisfaction Survey, conducted between March and April 2025. A total of 41,136 customers were invited to participate in the survey, and 11,366 responded, resulting in a response rate of 28%.
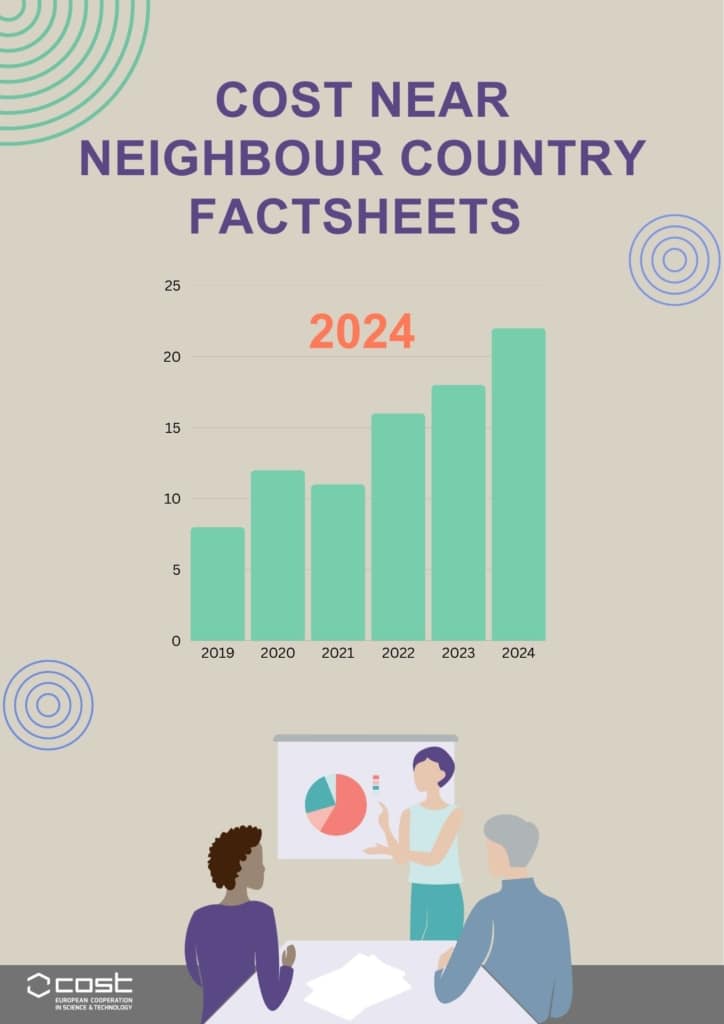
Near Neighbour Country Factsheets 2024
Countries covered: Algeria, Azerbaijan, Egypt, Jordan, Kosovo, Libya, Morocco, Palestine and Tunisia.
The NNC Factsheets 2024 highlight the growing involvement of nine Near Neighbour Countries in COST Actions, showing their increased participation in networking activities and research collaboration from 2019 to 2024. Researchers from these countries are actively contributing as secondary proposers in the COST Open calls and participating in a wide range of Actions across various fields, including health, sustainability, artificial intelligence, and education. Testimonials from participants emphasise the value of COST in expanding professional networks, fostering interdisciplinary cooperation, and enhancing scientific visibility.

Artificial Intelligence Paradigms for Next-Generation Metal–Organic Framework Research
In this perspective, we discuss the latest developments in machine-learning and deep-learning research on metal organic framework (MOF) materials and reflect on how their utilization has evolved within the large language models (LLMs) domain. We explore future benefits to accelerate and automate materials development research.
